Find amazing courses
Popular Courses
New Courses
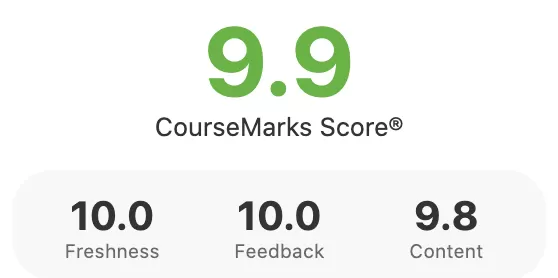
Independent Ratings
We evaluate the course on the basis of 18 signals to show you the best possible course in 13,000 topics. We have analysed 75,000 courses and found the 18 most important signals, such as the length of the videos, the ratio between the number students and the number of reviews, how detailed the description is. We have put everything into a final number so that you can find the high quality courses faster.
Keep exploring, keep learning.
Trending topics
Share Classbaze.com
Share on facebook
Facebook
Share on twitter
Twitter
Share on linkedin
LinkedIn
Share on tumblr
Tumblr
Share on pinterest
Pinterest
Share on telegram
Telegram
Share on digg
Digg
Share on whatsapp
WhatsApp
Share on email
Email